All Resources
All Resources
Filter by:
Services
Topics

- Device Lifecycle Services
- Apple
The Mac Management Playbook: 8 Steps to Deployment at Scale
By combining best practices with Compucom’s expertise and FLO Framework, enterprises unlock the full potential of their Mac devices: better…
READ MORE
- Device Lifecycle Services
- Apple
Full Lifecycle, Full Visibility: Maximizing the Value of Mac in the Enterprise
Macs are increasingly vital in today’s enterprise, but their true value is unlocked through strategic lifecycle management. This blog explores…
READ MORE

- Device Lifecycle Services
- Apple
Mac in the Enterprise — Myth vs. Reality: Debunking the Top Barriers to Adoption
Mac empowers organizations to work smarter, safer, and more efficiently. The myths have been busted. The reality? Mac means business.…
READ MORE

- Device Lifecycle Services
- Maturity Assessments
Maturity Assessments Set a Clear Path to IT Modernization
As your business navigates today’s uncertainty, knowing where your IT capabilities stand against industry maturity standards — and having expert…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Opportunity in Uncertainty: Leveraging Data for Fearless Decision-Making
Your IT environment holds the answers to making fearless decisions — especially when the world feels unpredictable. We’ve built our…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Opportunity in Uncertainty: Turning 6 Top IT Challenges into Strategic Advantages
In 2025’s uncertain landscape, IT challenges like economic instability, cybersecurity threats, and AI overload are pushing businesses to adapt fast.…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Navigating Uncertainty: Mitigate Risk and Unlock Opportunity with Strategic IT Sourcing
Unpredictable markets increase IT sourcing risk. Compucom’s strategic IT sourcing empowers your business to better navigate shifting conditions, optimize costs,…
READ MORE
- Managed Services and IT Support
- Full Lifecycle Observability
Future-Ready IT: Strategies to Optimize, Adapt, and Lead Through Uncertainty
In a world full of uncertainty, your company can thrive by focusing on these five key areas: optimizing your IT…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Reimagining IT with the FLO Framework: Inside Compucom’s Geordi Center for Interactive Managed Services and Digital Workplace Solutions
During the QKS Group’s recent visit to Compucom’s New Jersey office, we explored the Geordi Center, a collaboration studio designed…
READ MORE

- Device Lifecycle Services
- Apple
The Mac Management Playbook: 8 Steps to Deployment at Scale
By combining best practices with Compucom’s expertise and FLO Framework, enterprises unlock the full potential of their Mac devices: better…
READ MORE

- Device Lifecycle Services
- Apple
Full Lifecycle, Full Visibility: Maximizing the Value of Mac in the Enterprise
Macs are increasingly vital in today’s enterprise, but their true value is unlocked through strategic lifecycle management. This blog explores…
READ MORE

- Device Lifecycle Services
- Apple
Mac in the Enterprise — Myth vs. Reality: Debunking the Top Barriers to Adoption
Mac empowers organizations to work smarter, safer, and more efficiently. The myths have been busted. The reality? Mac means business.…
READ MORE

- Device Lifecycle Services
- Maturity Assessments
Maturity Assessments Set a Clear Path to IT Modernization
As your business navigates today’s uncertainty, knowing where your IT capabilities stand against industry maturity standards — and having expert…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Opportunity in Uncertainty: Leveraging Data for Fearless Decision-Making
Your IT environment holds the answers to making fearless decisions — especially when the world feels unpredictable. We’ve built our…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Opportunity in Uncertainty: Turning 6 Top IT Challenges into Strategic Advantages
In 2025’s uncertain landscape, IT challenges like economic instability, cybersecurity threats, and AI overload are pushing businesses to adapt fast.…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Navigating Uncertainty: Mitigate Risk and Unlock Opportunity with Strategic IT Sourcing
Unpredictable markets increase IT sourcing risk. Compucom’s strategic IT sourcing empowers your business to better navigate shifting conditions, optimize costs,…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Future-Ready IT: Strategies to Optimize, Adapt, and Lead Through Uncertainty
In a world full of uncertainty, your company can thrive by focusing on these five key areas: optimizing your IT…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Reimagining IT with the FLO Framework: Inside Compucom’s Geordi Center for Interactive Managed Services and Digital Workplace Solutions
During the QKS Group’s recent visit to Compucom’s New Jersey office, we explored the Geordi Center, a collaboration studio designed…
READ MORE

- Managed Services and IT Support
- Advanced Technology
Opportunity in Uncertainty: Optimize Your Remote, Hybrid, or In-Office Setup
Whether your company has landed on remote work, hybrid setups, or return to office (RTO), each model presents unique IT…
READ MORE

- Device Lifecycle Services
- Apple
The Mac Management Playbook: 8 Steps to Deployment at Scale
By combining best practices with Compucom’s expertise and FLO Framework, enterprises unlock the full potential of their Mac devices: better…
READ MORE

- Device Lifecycle Services
- Apple
Full Lifecycle, Full Visibility: Maximizing the Value of Mac in the Enterprise
Macs are increasingly vital in today’s enterprise, but their true value is unlocked through strategic lifecycle management. This blog explores…
READ MORE

- Device Lifecycle Services
- Apple
Mac in the Enterprise — Myth vs. Reality: Debunking the Top Barriers to Adoption
Mac empowers organizations to work smarter, safer, and more efficiently. The myths have been busted. The reality? Mac means business.…
READ MORE

- Device Lifecycle Services
- Maturity Assessments
Maturity Assessments Set a Clear Path to IT Modernization
As your business navigates today’s uncertainty, knowing where your IT capabilities stand against industry maturity standards — and having expert…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Opportunity in Uncertainty: Leveraging Data for Fearless Decision-Making
Your IT environment holds the answers to making fearless decisions — especially when the world feels unpredictable. We’ve built our…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Opportunity in Uncertainty: Turning 6 Top IT Challenges into Strategic Advantages
In 2025’s uncertain landscape, IT challenges like economic instability, cybersecurity threats, and AI overload are pushing businesses to adapt fast.…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Navigating Uncertainty: Mitigate Risk and Unlock Opportunity with Strategic IT Sourcing
Unpredictable markets increase IT sourcing risk. Compucom’s strategic IT sourcing empowers your business to better navigate shifting conditions, optimize costs,…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Future-Ready IT: Strategies to Optimize, Adapt, and Lead Through Uncertainty
In a world full of uncertainty, your company can thrive by focusing on these five key areas: optimizing your IT…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Reimagining IT with the FLO Framework: Inside Compucom’s Geordi Center for Interactive Managed Services and Digital Workplace Solutions
During the QKS Group’s recent visit to Compucom’s New Jersey office, we explored the Geordi Center, a collaboration studio designed…
READ MORE

- Managed Services and IT Support
- Advanced Technology
Opportunity in Uncertainty: Optimize Your Remote, Hybrid, or In-Office Setup
Whether your company has landed on remote work, hybrid setups, or return to office (RTO), each model presents unique IT…
READ MORE

- Projects and Professional Services
- IT Staffing
9 Ways Strategic IT Staffing Empowers Organizations
The benefits of IT Staffing. Read how two of Compucom’s talented contractors—David A. and Daniel S. — are proof of…
READ MORE

- Technology Sourcing Services
- Full Lifecycle Observability
Case Studies: Asset Intelligence and Endpoint Compliance Made Easy
Two FLO Framework case studies: 65% improvement in endpoint compliance, 40% boost in asset intelligence — in just 60 days.…
READ MORE

- Device Lifecycle Services
- Full Lifecycle Observability
AI and the Enterprise: The Future of IT Management
Compucom is an AI-forward company. We leverage AI internally and, as a managed services provider (MSP) dedicated to continuously increasing…
READ MORE

- Device Lifecycle Services
- Full Lifecycle Observability
Exploring the Opportunities and Obstacles of AI in the Enterprise
AI is already redefining many aspects of the enterprise, and leaders face a critical question – where and how should…
READ MORE
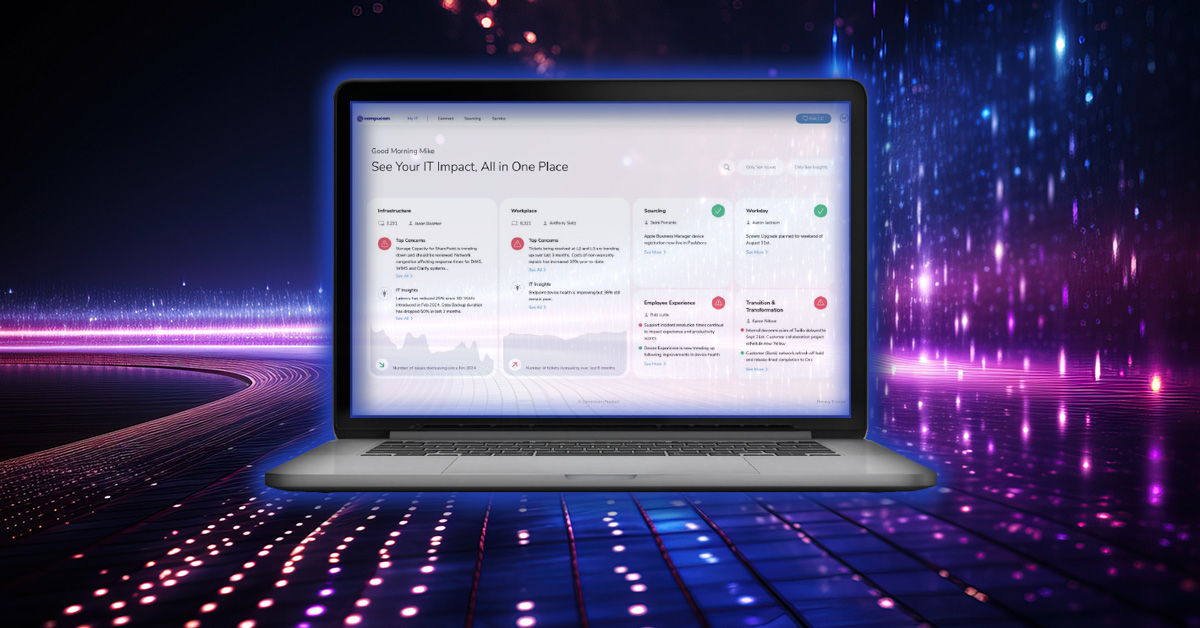
- Device Lifecycle Services
- Full Lifecycle Observability
One Dashboard to Rule Them All: Strategic IT Excellence with Full Lifecycle Observability
At Compucom, we define Full Lifecycle Observability as the ability to understand what happens throughout your company’s entire IT environment,…
READ MORE

- Managed Services and IT Support
- Full Lifecycle Observability
Transforming IT Operations with Full Lifecycle Observability: How Compucom’s FLO Framework Redefines Data-Driven Efficiency
Compucom’s Full Lifecycle Observability Framework (FLO Framework) stands tall with a transformative approach for leveraging data, AI-driven insights, and automation…
READ MORE
Explore by Topics
News

July 22, 2025
Compucom Named a Finalist in CRN’s Inaugural Best of the Channel Awards
Compucom is proud to share that CRN®, a brand of The Channel Company, has recognized it as a finalist in…
READ MORE
READ MORE

May 6, 2025
Compucom Achieves Significant Sustainability Milestones in Latest EcoVadis Study
Compucom announces significant year-over-year improvements in its EcoVadis sustainability performance, This year, Compucom achieved a dramatic 20% increase in its…
READ MORE
READ MORE

March 31, 2025
Compucom Selects OpsRamp to Deliver Full Lifecycle Observability Services for Customers
Compucom has selected OpsRamp, a Hewlett Packard Enterprise company, to power its entire services business with full lifecycle IT monitoring,…
READ MORE
READ MORE

July 22, 2025
Compucom Named a Finalist in CRN’s Inaugural Best of the Channel Awards
Compucom is proud to share that CRN®, a brand of The Channel Company, has recognized it as a finalist in…
READ MORE

May 6, 2025
Compucom Achieves Significant Sustainability Milestones in Latest EcoVadis Study
Compucom announces significant year-over-year improvements in its EcoVadis sustainability performance, This year, Compucom achieved a dramatic 20% increase in its…
READ MORE

March 31, 2025
Compucom Selects OpsRamp to Deliver Full Lifecycle Observability Services for Customers
Compucom has selected OpsRamp, a Hewlett Packard Enterprise company, to power its entire services business with full lifecycle IT monitoring,…
READ MORE